Today, we’re looking into a scam known as the Pig Butchering Scam.
The internet offers limitless opportunities not just for legitimate businesses but scammers as well. And scammers don’t spare efforts and resources to get their hands on your hard-earned money.
Peer-to-peer cryptocurrencies, some completely anonymous, have made it possible for online scammers to extract money from their victims without creating a paper trail. Cryptocurrencies like Bitcoin are pseudo-anonymous, however. As such, with the right tools, specialists can trace transactions and discover the identities and locations of the perpetrators.
Pig butchering scams may work without cryptocurrencies, but due to the convenience they offer, criminals often prefer to use cryptocurrencies as a medium of payment to fleece their victims. Once someone sends a crypto payment, the wronged party can’t recover it directly. Crypto tracing and asset recovery specialists can recover funds sent through pseudo-anonymous blockchains, but it takes time and effort.

What is a Pig Butchering Scam, and Why Do They Call it That?
A text scam called pig butchering started making the rounds in China during the COVID-19 pandemic. From there, it quickly gained traction all over the world. The scam is elaborate, requiring patience and long-term commitment from the scammers.
The perpetrators of the pig butchering scam start by cold-contacting victims, striking up conversations, and gaining their trust. When they deem they have “fattened the hog” enough, they try to “butcher” it by peddling an investment scam or thinking of another way to get the victim to send them money.
Scammers steal tens of billions of dollars from their victims every year. And the pig butchering scam is responsible for a large portion of the lost funds. Creative scammers can combine their pig butchering schemes with romance scams, cryptocurrency investments, other investment platforms, or whatever else they may think fits the context.
The scope of the pig butchering scam is wide. It can serve as a framework for many other types of scams. Pig butchering scammers can even exploit links to human trafficking. In Southeast Asia, criminals have forced victims of human trafficking to take part in pig butchering scams against their will.
Criminals often run well-organized scam sweatshops, where hundreds of human trafficking victims spend their days trying to steal money from unsuspecting internet, social media, and phone users.
How does a pig butchering scam work? What do the coerced or willing scammers do in their sweatshops all day?
The Anatomy of a Pig Butchering Scam
Pig butchering scams require scammers to contact victims and build trust. This is the stage of the scam where they sow their seeds or begin to fatten their hogs.
Step 1: Setting Up a Fake Identity
Before they can set their schemes in motion, scammers need a phony but credible online persona. This can be an Instagram account featuring pictures of attractive people in situations suggestive of great personal success and glamorous lifestyles.
The pictures scammers use are often stolen. In some cases, reverse image searches can reveal the sources of the pictures to victims, thus alerting them to the scam. The point is, however, that scammers target gullible people who aren’t tech-savvy and are more likely to take what they see online at face value.
With the profile set up, scammers may buy followers to lend their efforts additional credibility. Then, they are ready to swing into action.
Step 2: Making Contact
Social networking and dating sites are the preferred roaming grounds of pig butchering scammers. They have an abundance of potential victims on these channels. That doesn’t mean they won’t use other means to contact people. Some may resort to simply sending text messages to phone numbers they can buy from various sources.
Apps like Viber or WhatsApp also work for this purpose.
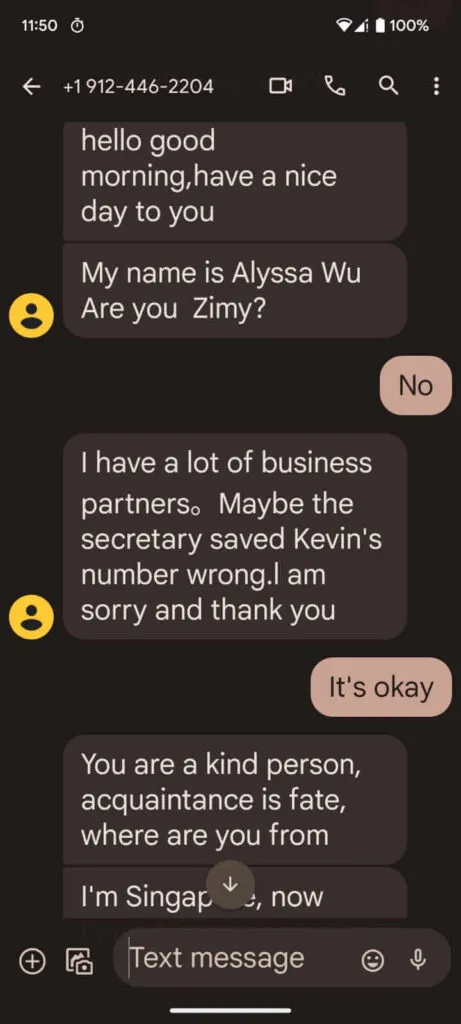
The perpetrators pretend to contact the victims by mistake. They may say they have typed in the wrong number, etc.
Once they have secured a communication channel with the would-be victim, scammers move on to the next step: building rapport.
Step 3: Building Trust
Pig butchering scams always begin with benign, light-hearted chats about work, family, etc. Even during this stage, however, scammers mine for personal information they can use later. They record everything the victims tell them. At the same time, they feed the victims fabricated information about their lives, etc.
They try to establish rapport by fabricating circumstances that make them relatable, even similar to their victims. If the victim is someone taking care of an elderly parent or grandparent, out come the stories about how they, too, struggle with similar problems, despite their obvious success.
Step 4: The Pivot
At first, scammers cautiously brag about their financial success. Later, as they build interest on the part of the victims, their stories grow bolder. And they whip out screenshots of investment accounts containing fabulous amounts of money. Mind you, these accounts are all fake, as are the funds they purportedly contain.
Trading platforms and online trading are scammers’ preferred methods to extract money from their victims. They use the popularity of MetaTrader’s MT4 and MT5 trading platforms to lend credibility to their claims. Even though these platforms are legitimate, the brokers with whom they claim they’re trading are nothing more than scams.
Once they deposit real money into a fake account, victims have fallen for the scam. Instead of deposits to alleged trading accounts, scammers may ask victims for money as part of a romance scam. They may figure out other stories and angles to get their victims to send them money.
Step 5: Offering Help with Investments
Posing as seasoned professionals, scammers offer to ”help” their victims trade and attain the same success they claim they have. Sometimes, scammers throw another “hook” into the mix, getting victims to make a small deposit in the name of caution. That small initial deposit will net a huge profit, igniting greed in the victims.
Having seen direct proof that the scheme works, the victims are eager to hike the stakes and send the scammers substantial sums.
Step 6: Offering “Proof”
Scammers may even allow their victims to withdraw their initial investments. With such indubitable proof in their hands, victims tend to overlook all red flags and warning signs. Scammers only let go of the cash to grab more eventually.
Step 7: Getting Victims to Go All-in
Once greed gets hold of them, some victims will mortgage their homes or tap into their retirement savings. Convinced they are investing in a legitimate scheme, they go all-in.
This is the holy grail of scammers. Squeezing people for every cent they have.
Step 8: Cashing in on Victims’ Desperation
Some scammers will stop at nothing. Once the victims realize they’ve been tricked, they begin threatening and begging the scammers. The pig butchering specialists may promise that there is a way to get their money back, but, of course, first, they must send more money.
Step 9: Cutting Off the Victims
Pig butchering scammers only let their victims off the hook once they realize they can’t squeeze more money out of them. It is not uncommon for scammers to threaten or insult their victims before they go silent. Their fake brokerages and websites often disappear after they cut off their victims.

Pig Butchering Scam Warning Signs
Web- and tech-savvy people do not have problems recognizing a pig butchering scam, but many web users fall into neither of those categories. Here are some red flags that can help you avoid becoming the victim of a pig butchering scam.
Someone cold-contacts you, claiming a “wrong number” mishap or just chatting you up out of the blue.
A person you met online suddenly starts bragging and talking about financial matters, possibly crypto investments.
- A dating site contact “falls in love” with you suspiciously quickly.
- A contact you’ve had for a while tries to manipulate you emotionally.
- Your new online friend urges you to invest in a “guaranteed” scheme.
- The trading platform they urge you to use looks suspiciously minimalistic.
- The person who urges you to start investing helps you deposit and invest.
- Your small initial investment generates a profit quickly.
- The “broker” asks you for fees and hefty taxes to allow withdrawals.
As a rule of thumb, remember this: everything that looks too good to be true is a construct someone has created to fool you. There are no exceptions.
How Human Trafficking and Real-life Crime Intertwine with Online Scams
Organized crime perpetrates online scams, relying on tens of thousands of victims of human trafficking in Southeast Asia to keep the wheels of the pig butchering scams turning.
Criminals buy and sell human beings through Telegram channels as one would buy and sell used furniture on Craigslist. Traffickers run sweatshops and rely on forced labor to lend their scams an industrial scope.
Human traffickers acquire their victims through ads for allegedly lucrative jobs. People living in poor areas find these offers enticing and often fall for the trap. The poverty lands them squarely at the mercy of their captors, whose bidding they must do if they ever hope to escape their situation.
Many of these victims work pig butchering scams for their captors against their will.
Can You Recover Money Lost To Pig Butchering Scams?
CNC Intelligence plays a pivotal role in aiding victims of the Pig Butchering Scam and supporting law professionals, such as police and law enforcement agencies, in tackling these complex cases. Our expertise spans cryptocurrency forensics, cyber investigations, and asset recovery, positioning us as a valuable resource in combating this sophisticated fraud.
For individuals who have fallen prey to the Pig Butchering Scam, CNC Intelligence offers specialized services in tracing and assisting law enforcement in recovering lost assets. We utilize cutting-edge technology in cryptocurrency tracing, enabling us to track the flow of stolen funds and assist in their recovery. Beyond asset recovery, CNC Intelligence conducts comprehensive investigations to unravel the intricacies of the scam, gathering vital evidence that can be crucial in legal proceedings. We also provide essential guidance and support to victims, advising on securing their remaining assets and protecting their identity post-scam.
Law professionals and enforcement agencies benefit greatly from CNC Intelligence’s expertise in cryptocurrency tracing. This skill is particularly vital for tracking down perpetrators in scams involving cryptocurrencies. We offer actionable intelligence and evidence gathering, essential for law enforcement agencies to pursue legal action against scammers effectively. In addition to our investigative services, CNC Intelligence provides training and resources to law professionals. This training enhances their understanding of cryptocurrency scams and improves their investigative techniques, crucial in the rapidly evolving landscape of cybercrime.
Moreover, CNC Intelligence assists in the legal process by helping draft subpoenas and providing expert witness services. Our support is invaluable for legal professionals in building robust cases against scammers. Our multifaceted approach, combining technological prowess with an understanding of legal processes, makes CNC Intelligence a crucial ally for both victims seeking to recover their assets and law professionals aiming to apprehend and prosecute perpetrators of the Pig Butchering Scam.
Case Study: Recovering $1.6 Million from a Pig Butchering Scam
Here, we detail a case where CNC Intelligence helped a New England resident recover $1.6 million from a pig butchering scam.
Robert, a New England resident, was contacted by a scammer on a dating site who introduced him to a supposed expert trader. Using a fraudulent trading app that mimicked legitimate platforms, the scammer showed Robert fake gains, convincing him to invest more. Eventually, Robert lost $1.6 million in a single, fabricated catastrophic trade.
CNC Intelligence was enlisted to trace and recover Robert’s assets. Utilizing advanced blockchain analysis tools, they tracked the stolen funds to accounts in Hong Kong. CNC Intelligence then coordinated with the law firm Hauzen LLP to secure injunctions and pursue legal proceedings, leading to the recovery of the assets.
Hauzen LLP obtained injunctions to freeze the identified accounts and engaged in extensive legal proceedings to recover the funds. Despite legal challenges and a lengthy process of over a year and a half, the courts ruled in favor of Robert, releasing the frozen assets. CNC Intelligence’s precise asset tracing and collaboration with legal professionals were pivotal to this success.
Conclusion
The Pig Butchering Scam represents a harrowing reminder of the darker side of the digital age, where the convergence of technology, human vulnerability, and criminal intent creates a potent recipe for fraud. This scam, originating in China during the COVID-19 pandemic, rapidly gained global notoriety, exploiting the interconnectedness of our online world. Its success lies not just in its elaborate design but in its ability to adapt and blend into various online platforms, making it a chameleon in the world of cyber fraud.
The essence of the Pig Butchering Scam lies in its methodical approach to building trust and manipulating emotions. Scammers painstakingly set up fake identities, often leveraging the allure of financial success and a glamorous lifestyle to lure victims. They infiltrate social networks and dating sites and even send direct messages, always with the intent of establishing a connection under false pretenses. The initial conversations are benign, designed to disarm and gather personal information, laying the groundwork for the scam.
The pivot toward financial discussions is subtle yet calculated. Scammers flaunt their fabricated financial prowess, using fake investment accounts to dazzle and entice their victims. The lure of quick, high returns is the bait, and many fall prey to the illusion of a legitimate investment opportunity. The scam evolves from small initial investments, showing astonishing returns, to convincing victims to invest substantial sums, sometimes involving their life savings.
But the Pig Butchering Scam is more than just a financial fraud; it is a mirror reflecting the complex interplay of online scams and real-world crimes like human trafficking. In Southeast Asia, human trafficking victims are coerced into perpetrating these scams, revealing a sinister underbelly where cybercrime and human rights violations intertwine. Organized crime syndicates run these operations, turning innocent individuals into unwilling accomplices in their fraudulent schemes.
The endgame of the Pig Butchering Scam is as ruthless as it is heartbreaking. Once the scammers have extracted as much as they can, they sever all ties, leaving victims financially and emotionally devastated. This brutal conclusion serves as a stark reminder of the scam’s true nature—a systematic exploitation of trust for financial gain.
In the wake of such sophisticated and devastating scams, the importance of vigilance and skepticism cannot be overstated. Recognizing the red flags—unsolicited contacts, sudden financial discussions, too-good-to-be-true investment opportunities—is crucial. The digital world offers immense opportunities but also harbors threats that require constant awareness and caution.
If you believe you are a victim of this cryptocurrency scam, report it to the United States Federal Trade Commission (FTC), the Internet Crime Center (IC3), your Federal Bureau of Investigation (FBI) local office, and your local police. The longer you wait, the harder it’s going to be to recover the funds.
Are you a victim of an online scam? Schedule a FREE consultation with us and find out if we are able to help you get your money back.
When you comment, your name, comment, and timestamp will be public. We also store this data, which may be used for research or content creation in accordance with our Privacy Policy. By commenting, you consent to these terms.