Can you recover crypto funds you lost to a scam or theft? Can anyone help you track down the people behind the crime and get your coins back? Is Bitcoin Traceable? The answer is yes, yes, and yes!

As blockchain analytics solutions grow more complex and powerful, bitcoin is becoming increasingly traceable.
How can you track a Bitcoin address?
Are Bitcoin wallets traceable?
How do digital asset recovery experts trace the path stolen digital funds take through the crypto world?
Find out all that and more below.
How Traceable is Bitcoin?
Are Bitcoin transactions anonymous?
If you’re interested in Bitcoin as a peer-to-peer vehicle to exchange value, you’ve probably read that it is a pseudo-anonymous payment solution.
What does that mean?
And why is it not fully anonymous?
Bitcoin users don’t have to provide their names or verify their identities to use the currency.
All they need is a wallet and someone willing to send them Bitcoin.
To receive Bitcoin, users must give their peers a public address.
The address looks like this: bc1qjg6qtsztnk4e6k05wmng3nkcvvjlwqpraj6l0u.
We call this a “public” address because everyone can see it.
The blockchain broadcasts every transaction.
And everyone using a blockchain explorer can see every single transaction that has ever happened on the Bitcoin blockchain.
The blockchain is transparent but not easy to read.
If you open a blockchain explorer, this is what you’ll see:
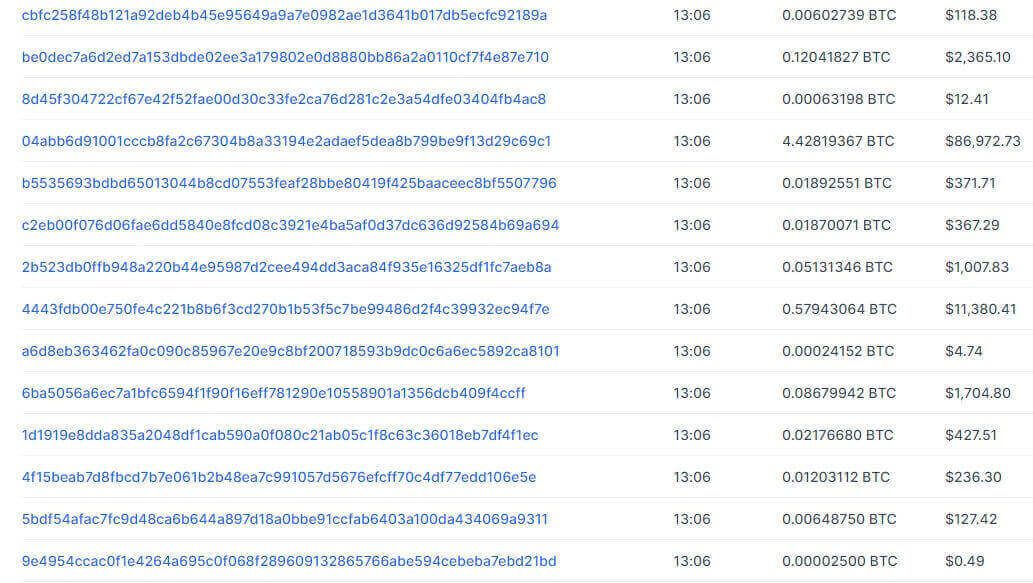
In addition to the crypto transaction hash, transactions carry a wealth of data.
And, through a blockchain explorer, you can read it all.
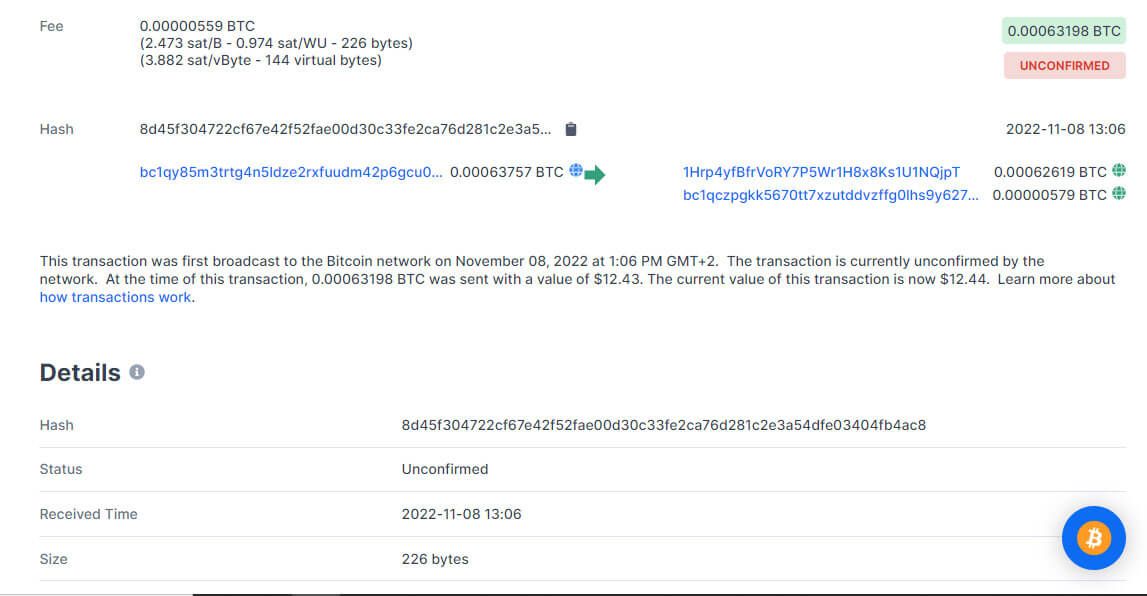
You don’t have to be an expert to see the sending address, the receiving address, the amount of the transaction, its exact time and date, and its status on the network.
You can track Bitcoin transactions without specialized tools and expertise.
Now, imagine what asset recovery specialists can do with advanced, dedicated tracking tools and expertise.
The data you can obtain through a blockchain explorer may not contain any references to the identities of the parties involved in a transaction.
It is generous nonetheless.
Here’s what it tells us.
- The TxID is the transaction hash that serves as an identifier for the transaction on the Bitcoin blockchain.
- The address of the sender.
- The address of the recipient.
- The address to which the network returned the unspent bitcoin resulting from the transaction. This address belongs to the sender as well.
- The amounts transacted in Bitcoin and their value in fiat at the moment of confirmation.
- The time that the Bitcoin blockchain accepted the block to which the transaction belongs. The time of transaction differs from this Unix timestamp. The average confirmation time can range from 5 to 45 minutes or even more.
Learning how to trace cryptocurrency is not easy, but more and more people and organizations see the utility in developing crypto-tracing skills.
How Do Specialists Trace Bitcoin?
Crypto tracing specialists answer questions most blockchain explorer users can’t.
- Who are the sending and receiving entities?
- What cryptocurrency addresses are they using?
- Why do the transactions happen?
- Where are the people behind the transactions?
- Where are the funds the perpetrators of a crypto theft have appropriated?
How can crypto tracing and asset recovery professionals answer these questions?
They use a set of advanced tools, cooperate with crypto exchanges, and cooperate with law enforcement agencies around the world.
And they don’t shy away from a real-life investigation to complement their online capabilities.
Here’s what crypto tracing specialists can find out from information available online.
Cluster Analysis
Through cluster analysis, blockchain investigators determine the addresses that belong to the same entity.
Tracking one address can yield a trove of information.
Tracking multiple addresses can yield much more, however.
When the goal is to lift the veil of anonymity from transactions, every bit of extra information matters.
Investigators can run algorithms on the entirety of the blockchain. They can analyze:
- Behavioral patterns
- Change addresses
- Co-spends
- Various obfuscation techniques
- Peel chains that attempt to mask large transfers through many smaller ones
Attribution Data and Identification
Attribution data is a preliminary attempt to link crypto addresses and assets to entities.
The systems that establish connections at this stage rarely link assets or addresses to certain people.
They find links between addresses or address clusters and fraud schemes, criminal groups, and exchanges or mixers the criminals may have used to launder the proceeds of their activities.
Once investigators identify entities behind address clusters, they can refine identification through other automatic and manual techniques.
Targeting IP Addresses
“Listening” for IP addresses involved in certain transactions allows investigators to establish the geographic locations of the people and entities behind the transfers.
Surveillance systems can run network nodes.
They can use these as access points to filter IP addresses as transactions happen.
Making Sense of Transactional Data
Investigators compile the data they collect on transactions into charts they can analyze visually.
The analysis aims to identify behavior patterns and link transactions to various entities and people.
Transaction mapping reveals interactions between criminals, cryptocurrency exchanges, and mixer services.
It can also help investigators find the endpoints of transactions.
Through transaction mapping, investigators can peer through advanced obfuscation techniques like peel chains and layering.
Layering is a cryptocurrency laundering technique.
Criminals transfer the funds they have stolen through a jumble of intermediary addresses and third-party services.
The process tends to culminate in a single destination where all the laundered funds land.
Through layering, crypto criminals increase the length of the crypto trail, slowing the investigation while hoping to throw investigators off course.
Thieves may use a peel chain to gradually cash out a larger cryptocurrency cache.
They make several smaller transfers to cryptocurrency exchanges, proceeding to cash them out.
Eventually, they cash out the entire haul, little by little.
Through charting, cryptocurrency investigators can piece together the crypto trail, regardless of its complexity.
Advanced charting solutions automate data collection, allowing investigators to process more information than they could by manually sifting through the data they grab from blockchain explorers.
Using specialized tools, blockchain data specialists can establish sending and receiving exposure profiles for address clusters and illustrate them visually as charts.
Risk-profiling
Automated investigative tools can compile a risk score for addresses, considering their interactions with known criminal entities, mixers, exchanges, etc.
The resulting score tells investigators whether these addresses are involved in fraud.
Establishing Targets for Subpoenas
Authorities have long considered Bitcoin’s pseudo-anonymity a risk.
They have passed laws that require companies operating crypto services to identify every one of their customers.
Most exchanges observe Know Your Customer (KYC) and Anti Money Laundering (AML) policies.
If you have ever interacted with an exchange, that exchange has your personal data.
Investigators know how to track a Bitcoin scammer.
If you are one and use your exchange account to launder your proceeds or cash them out, you will instantly reveal your identity to the asset recovery specialists.
Once they find out that a suspect may have interacted with a KYC-compliant exchange, DeFi firm, or virtual asset service provider, investigators obtain criminal warrants or civil subpoenas.
These tools allow them to have the exchange reveal the personal identification data of suspects.
Finding targets of subpoenas and pursuing the leads they have through them is an essential step for cryptocurrency crime investigators.
Total Transactions
Once investigators identify a cluster of Bitcoin addresses involved in fraud, they can determine the size of the crime and the number of victims.
They can share the information they have deduced and wrap up more criminals, recovering assets for more victims.
They can also enable class-action lawsuits in civil courts.
Identifying Addresses for Seizure and Garnishing
Crypto recovery specialists look for Bitcoin addresses storing significant value tied to the crimes and perpetrators.
These addresses represent prime targets for garnishing and seizure warrants.
By seizing these addresses, investigators can recover assets for their clients and other victims of crypto theft.
Freezing the stolen funds is essential, as it can prevent the criminals from dissipating the assets and preventing the recovery of funds.
Cryptocurrencies are global.
The criminals who steal your funds may not reside in your legal jurisdiction.
Freezing addresses requires cooperation with local authorities and law enforcement.
Professional investigators can liaise with local law enforcement in many jurisdictions worldwide.
They can get seizure warrants and recover assets within a legal framework.
If Bitcoin is Traceable, Why Do Criminals Use it?
The complexity of crypto crime can vary.
Some crypto criminals are the equivalents of petty thieves who defraud a few people and try to cash out quickly without performing advanced stunts to hide their trail.
Others are confident in their abilities to obfuscate their criminal trail and deem Bitcoin a private enough solution for value transfer.
Bitcoin is a solid global online currency.
Its peer-to-peer status makes it ideal for online scams.
Once criminals get their hands on your money, you can’t get it back.
It’s like giving cash to someone you don’t know and can’t see.
It is easy to see why all this is attractive to criminals.
Law enforcement and cryptocurrency tracing specialists are increasingly able to trace bitcoins.
And they can identify crypto criminals, exposing their entire criminal history through the blockchain.
More privacy-oriented crypto solutions may be more attractive to criminals.
But it can be more difficult to convince someone to buy some shady, barely-known crypto coin than the highly accessible bitcoin.
Is Bitcoin Traceable by the IRS?
If you are thinking about using Bitcoin to avoid taxes, think again.
The IRS requires people to report crypto profits.
And it can trace crypto transfers.
The Internal Revenue Service also requires crypto exchanges and various trading platforms to report Form 1099-B and Form 1099-K.
Crypto users must account for cryptocurrency trading profits in their income tax returns.
If you want to avoid paying taxes for revenues you may derive from cryptocurrencies, try the legal path through Crypto IRAs and 401Ks.
Don’t use crypto to launder illicit money.
And don’t think you can escape crypto taxes.
The IRS has the resources to hire the best cryptocurrency tracing experts and purchase the best blockchain analysis tools.
Cooperating with law enforcement is not a challenge for the IRS.
Crypto exchanges like Kraken, Gemini, Coinbase, and Binance work directly with the IRS.
If you generate crypto income at any of these exchanges, they automatically report your activities to the tax collection agency.
If you receive tax forms from one of these exchanges, you can assume that the IRS also has a copy of it.
From the perspective of the IRS, crypto is not a currency but a taxable property.
Taxpayers now have to answer an extra question on Form 1040.
They must specify whether they have made crypto transactions in the current financial year.
Bottom Line: Is Bitcoin Traceable?
Bitcoin transactions are traceable.
However, bitcoin’s recent Taproot upgrade has made complex transactions impossible to tell apart from regular ones.
Lightning Network transactions show up on the main blockchain as single transactions.
Without Taproot, investigators could tell that they were complex transactions.
Taproot now makes that distinction impossible.
As technology evolves, so do the tools that allow investigators to apprehend criminals and recover stolen funds.
We offer complimentary consultations to determine if our Asset Tracing, Recovery Assistance, and Intelligence Services are suitable for your case.
When you comment, your name, comment, and timestamp will be public. We also store this data, which may be used for research or content creation, in accordance with our Privacy Policy. By commenting, you consent to these terms.
I have been scammed on 12/15/23
of 4,400.00
Order QHDIN6CL
Hello Freddie,
Thank you for reaching out and sharing your experience with us. We’re truly sorry to hear that you have been a victim of a scam. While we understand this is a difficult time for you, it’s important to note that our specialized cryptocurrency tracing services are typically geared towards cases involving larger sums.
However, we still encourage you to reach out for a consultation. Even though your case involves an amount below our usual threshold, we believe it’s essential to assess each situation individually. During the consultation, we can discuss the specifics of your case and see if there are ways we can assist or advise you.
Please visit our consultation page here: CNC Intelligence Consultation to schedule a time to speak with one of our experts. We’re committed to providing assistance where possible and guiding you towards the best course of action given your circumstances.
I am new to buying crypto on presale, I bought between $ 8000 to 10,000 of Kangamoon crypto during the presale in September and October, which was supposed to end in the last quarter, I presume December, now according to their website they are starting presale again with a new system switch, from all the comments that I have seen no one are able to see their tokens anymore, I am sure we all have been scammed, I know I won’t be able to get my money back but I would like to see them shut down before they get other people money, it’s not hard to see them scamming on the internet, I would say between September and October and just a couple articles in November they were burning the internet up with presale articles then they just stopped, as normal everyday people we don’t have the knowledge or tools to deal with this so I am asking for your help to track and shut them down before they steal more money from people. I don’t understand how so many different websites and articles we put up about the token when advertising presale, I would have thought someone would have recognized it was a scam and warned the public. Please help if you can or just ignore and delete,
Thank you , Bud Baylis
PS at least look into it and see if they are legitimate, I still have a little hope left
Dear Mr. Baylis,
Thank you for reaching out to us with your report regarding your experience with Kangamoon crypto. We appreciate you taking the time to share these details, and we recognize the importance of addressing your concerns.
Our team is reviewing the information you’ve provided and will be in touch with you to discuss the next steps. In the meantime, if you wish to expedite the process or have further information to share, we invite you to schedule a free consultation with us. You can do so by visiting our consultation page at https://cncintel.com/consultation
We understand the urgency and sensitivity of these matters and assure you of our commitment to professional and thorough investigation. Please feel free to reach out to us through the consultation link if you have any additional questions or need immediate assistance.
Thank you once again for contacting CNC Intelligence. We are here to assist you.