In this article, you will learn not only how to protect your identity online, but also why it is so important.
Identity theft has grown into one of the top consumer fraud types over the last couple of years.
According to information from the FTC in the US, identity theft-based crime doubled from 2019 to 2020.
The global pandemic sent many workers into home offices and online, and as a result, criminals shifted their activities online as well.
The pandemic-related benefits governments have been doling out have acted as incentives for criminals to steal identities and apply for benefits in someone else’s name.
The current trends promise nothing favorable for advocates of online privacy.
Online services demand more and more of our personal information.
Social networks and search engines shamelessly collect data on their users, profiling them, and often selling their sensitive information to third parties.
What is the personal information that makes up your identity?
What do you have to protect?
- Your full name and physical address
- Your date of birth
- Phone number
- Email address
- The school to which you went
- Any passwords you use to access any online services
- Everything about your bank accounts, credit cards, etc.
In this full-fledged war on privacy, how protect your identity online?
You don’t have to be an expert to realize that once you go online, you cannot insulate yourself from identity theft.
You will always be exposed to some degree.
You can, however, take measures to limit your exposure.
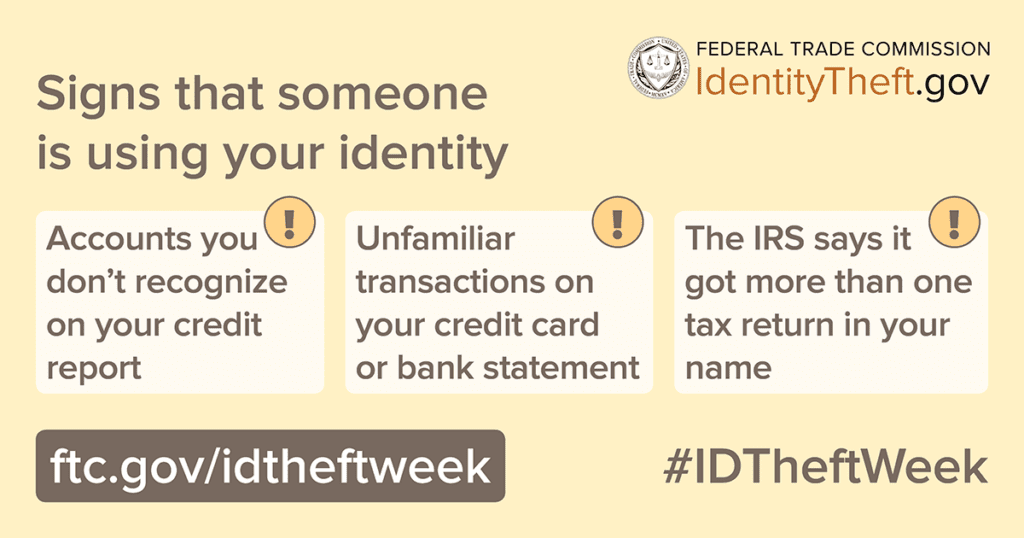
How to Tell if Someone Is Using Your Identity
Here’s how to protect your identity online:
1. Limit Email Spam and Avoid Malware
Keeping the software on the device you use to access the internet up to date is essential.
You may find the seemingly constant updates annoying, but you should know that skipping them will expose you to spammer botnet attacks.
Hackers prowl the internet looking for devices they can infect with malware.
Taking remote control of such devices, they can initiate spam attacks using your hardware.
Thus, you may find yourself in legal trouble or have your IP addresses banned.
If a hacker gains control of your device, he/she can siphon off all the information you keep on it.
So be careful what you choose to keep on your computer, tablet, phone, etc.
In addition to keeping your security software up to date, here’s what else you can do:
Find a way to detect and eliminate malware from your computer.
If you suspect foul play, immediately take your device offline.
Get an anti-malware program and eliminate the shady bits of code.
Report the incident to the appropriate authorities like the FTC, or the FBI.
Never settle for default passwords.
Hackers count on some people being lazy enough to leave their default passwords unaltered.
Change your default password to a more complex combination.
To limit the amount of email spam hitting your inbox, limit your exposure.
Use separate email addresses for work and personal correspondence.
Don’t make your email address available as the contact option of your website.
Have a dedicated, throw-away email for that purpose. Install a spam filter, report spam, and unsubscribe from email updates you don’t want or need.
Despite all these actions, some email spam may still end up in your inbox.
That is why it’s important to learn how to recognize a scam.
2. Learn to Recognize Scam and Phishing Attempts
Some email scam attempts are easy to spot, but others can be convincing.
If you have had your identity already compromised online, scammers can use the information to concoct credible schemes and victimize you.
The only way to ensure that you don’t fall for an online scam is to never click on a link in an email.
Not all scams aim to relieve you of money.
Some are after your personal information to steal your identity.
That email bearing the logo of your bank may be a legitimate one.
But it may also be a scam.
Never share personal information online with anyone unless you are positive that you are dealing with a legitimate, trustworthy party.
According to the FTC, the most popular scams you are likely to encounter online are:
- Online shopping scams.
- Business imposter scams.
- Government imposter scams.
- Fake check and romance scams.
- Work-at-home schemes and various other business opportunities.
- Credit counseling and debt settlement scams.
- Investment scams.
- Vacation scams.
- Fake tech support.
Online scammers are creative.
They may attempt to trick you in other ways as well.
Always be vigilant.
Generally, deals that are extremely advantageous, too good to be true are all scams.
3. Keep Your Eyes on Your Credit Reports
Scammers, spammers, identity thieves, hackers, and various other online crooks are after one thing: money.
Regardless of how convoluted their schemes are, they eventually boil down to you having to send someone money in some form.
Identity thieves may use the credit card information they steal from you to shop online in your name or take out cash advances.
If you keep your eyes on your credit reports, you can spot such activity and nip it in the bud.
Report any suspicious events to the appropriate authorities as soon as possible.
Pursue a resolution aggressively, and you can avoid a strike on your credit score.
Often, victims do not realize that online thieves have stolen their personal information.
You may not realize that you have become a victim of online identity theft before the perpetrators attempt to grab some money.
US law protects credit card users from fraud.
If you can spot suspicious activity and freeze your credit, you can head off more significant problems.
Be on the lookout for other credit-related signs of identity theft.
- You don’t receive bills and other essential mail.
- Your credit report contains inaccurate or false information. Your Social Security Number may be off. Your address may be fake, etc.
- You receive credit cards for which you never applied.
- Creditors contact you about bills you have never accrued.
4. Stay Away from Public WiFi
Public WiFi exposes you to more dangers than a private connection.
Such networks are unsecured, presenting an attractive opportunity for scammers, hackers, and other online evildoers.
Only make your purchases through reputable websites.
Make sure that the online shopping sites you use are indeed what they purport to be.
Use reputable and responsible online merchants.
Be aware of the risks of online shopping.
Whenever you buy something online, you have to share certain information with the vendor, even if you pay securely.
Most merchants keep your information on file, somewhere online.
Hackers can steal your information from online merchants, compromising your privacy and exposing you to never-ending bouts of scams, phishing, and blackmail.
5. Limit Your Participation in Social Media
Social media has revolutionized the way we communicate, relate to one another, and share information.
The temptation is always there to share more.
Resist it.
Be aware that anything you share through your social media profiles can and may be used against you.
Skilled online crooks know where to mine for personal information that they can exploit in various ways.
They can use it to make their scams more credible or track your whereabouts and orchestrate a more direct scheme of causing you financial harm.
6. How to Protect Your Identity Online by Using a Different Search Engine
Most of the search engines to which we turn by default have built businesses on tracking and profiling their users.
Many will readily sell such information to other parties.
Ditch such risky ways of locating information online and adopt search engines that do not track their users.
7. Browse in Private Mode
Nowadays, everyone is interested in what you do online.
Every time you log onto the internet and browse around, you leave a trail of potentially sensitive personal information that someone somewhere can turn against you in some form.
By using the incognito mode of your web browser, you avoid saving cookies, your browsing history, and the data you enter into forms.
You may also prevent websites from tracking your online activities.
Be aware, however, that the privacy-focused features of most popular web browsers are limited.
8. How to Protect Your Identity Online By Thinking Before Clicking
Your online browsing may take you to less savory corners of the internet, to pages that host links to sites that attempt to infect your device with spyware and malware.
Malicious links are not exclusive to unsolicited emails.
They may appear anywhere, especially if you use shady websites that offer illegal downloads, etc.
Stay away from such sites and do not engage in illegal online activities.
Before you click a link, hover your cursor over it and see where it takes you.
If you notice anything suspicious about it, refrain from clicking it.
9. Do Not Use Your Social Media Accounts to Sign in to an App
More and more apps and online services offer you the option to sign in with one of your social media accounts.
By doing so, you will give the app access to a treasure trove of personal information.
You will likely give it unfettered access to everything you have posted on your profile.
How to Protect Your Identity Online – Bottom Line
When it comes to sharing personal information, observe a policy of less is more.
The less information you share online, the more likely you will be to protect your identity successfully.
We offer complimentary consultations to determine if our Asset Tracing, Recovery Assistance, and Intelligence Services are suitable for your case.
When you comment, your name, comment, and timestamp will be public. We also store this data, which may be used for research or content creation in accordance with our Privacy Policy. By commenting, you consent to these terms.