This article explains how Clipboard Hijacking malware works, how it steals cryptocurrency during copy-paste actions, and how to detect, remove, and protect against it.
TL;DR: Clipboard Hijacking is a sneaky type of malware that swaps copied crypto wallet addresses with a scammer’s, tricking you into sending funds to the wrong place. It runs silently in the background and activates when you copy-paste an address. To stay safe, always double-check pasted addresses, avoid sketchy downloads, and run regular antivirus scans. Once crypto is sent, it can’t be recovered—so prevention is key.
Copy-Pasting is not as safe as we thought. With the rise of clipboard hijacker software, here are some guidelines to shield your crypto from these sneaky pickpockets!
Clipboard hijacking is a form of malware with the potential to make your life a living hell. In essence, it is a hidden crypto thief, which targets your computer’s (or cell phone!) clipboard whenever you copy-paste a wallet address. Upon copying, the malware swaps the desired address for that of a scammer, and if you’re not careful and check it upon pasting it, your crypto might vanish without a trace.
If you’ve lost crypto after copy-pasting an address, clipboard hijacker malware might be the reason. But never fear! This comprehensive guide will give you all the tools you need to combat this threat!
The Basics: What You Need to Know
What is clipboard hijacking?
It is malware that secretly swaps your copied data, like crypto wallet addresses, for malicious alternatives.
What does a clipboard hijacker do?
It infiltrates your computer and replaces crypto wallet addresses you copy for that of a thief.
What is the best way to detect clipboard malware?
Copy-paste a crypto wallet address onto your notepad, and compare it to the original. If the copied version is different, your device is infected.
Can you remove clipboard hijacking malware manually?
Yes! Check your task manager for strange applications, and the programs that run at startup. Installing and running an antivirus is highly recommended too.
How can I protect myself from clipboard hijackers?
Avoid downloading programs from sketchy websites, run regular scans with your antivirus, and always check wallet addresses when copy-pasting them.
What is Clipboard Hijacking?
Clipboard hijacking is a growing cybersecurity threat that targets a small but critical action: copy-pasting. We’re all conditioned to trust ctrl-c / ctrl-v as the safest form of transferring information from one place to another in the digital space, but clipboard hijacker malware is specifically designed to take advantage of this trust. Worst part is, in most cases, it works like a charm. Victims don’t even realise something went wrong until their cryptocurrency vanishes.
The malware in question is engineered to intercept and alter copied information, such as Bitcoin or Ethereum wallet addresses. It will run in the background of your device, be it a PC, macOS, Linux, and even smartphones like Android and, in some rare cases, jailbroken iPhones. It will either disguise itself as a legitimate program, like a Chrome extension, or run as a hidden process. Then, when you copy-paste a wallet address to do an exchange, the clipboard hijacker will swap the wallet address and send your crypto to an unknown attacker.
Furthermore, since blockchain transactions are irreversible, this method of “crypto pickpocketing” has become a favoured tool for thieves, so if your crypto disappeared after copy-pasting an address, clipboard hijacking malware might be the reason.
How Clipboard Hijacker Malware Works:
Clipboard hijacking works in a simple but effective. Generally speaking, it follows these steps:
- Infection: The clipboard hijacker malware finds its way into your device. It can be secretly bundled together with something you downloaded, or disguise itself as a legitimate app. It will set itself up to run at startup, or upon launching a specific application such as a web browser.
- Monitoring: The malware will sit silently in the background, scanning your clipboard. It will wait for the right moment to activate the clipboard hack.
- Trigger: When you copy something that looks like a crypto wallet address (such as a long alphanumeric string starting with 1,3 or bc1 for Bitcoin, 0x for Ethereum) the clipboard virus activates.
- Replacement: The clipboard malware changes the copied address for another. It can either replace it for one in a predetermined list included in its programming, or, more typically, fetch a new address dynamically from an online server.
- Theft: You paste what you think is the intended address to carry out the crypto exchange, but the funds are sent to a scammer instead.
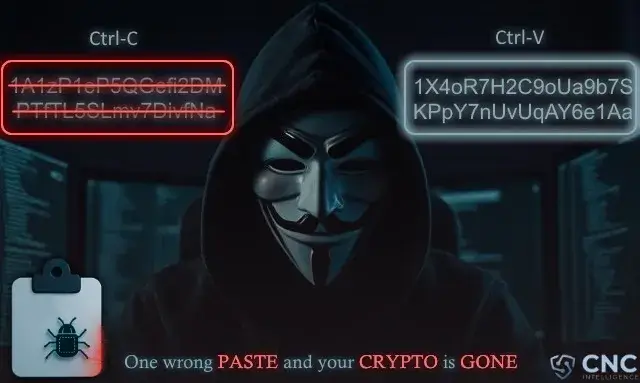
To give a basic example, let’s say you wish to sell $100 USD worth of Bitcoin to your friend. He sends you the following wallet address: 1A1zP1eP5QGefi2DMPTfTL5SLmv7DivfNa.
Upon copying it, however, it becomes: 1X4oR7H2C9oUa9b7SKPpY7nUvUqAY6e1Aa.
If you weren’t paying close attention, you might hit send, and the funds are gone.
How Can a Device be Infected?
Clipboard hijacker malware can infiltrate your device through several methods:
- Fake software: The clipboard malware disguises itself as a legitimate application, update, or tool, and is installed on your device when you run the .exe file. Browser extensions are a good example.
- Trojans: The hijacker comes bundled with another, seemingly harmless software, and secretly installs itself when you run the .exe file. This is particularly common with tools included in shady tutorials, such as those found on small Youtube channels.
- Phishing attacks: Emails or other messages with malicious attachments or links that trick you into clicking them, installing the malware upon doing so.
- Web exploits: Malicious scripts on compromised websites can alter clipboard contents, sometimes requiring user interaction like clicking a fake CAPTCHA.
Cryptocurrency Clipboard Hijackers: Why You Should Worry
The cryptocurrency ecosystem is the perfect target for clipboard hijacking malware. It is fast paced, completely reliant on an internet connection, and those who engage in crypto trading are often distracted by other, ever evolving variables, such as price fluctuations. Furthermore, cryptocurrency clipboard hijackers will take full advantage of the following:
- Irreversibility: Blockchain transactions cannot be reversed. Once you send cryptocurrencies to the wrong address, it’s gone. There is no bank or financial authority to call, and no refund button to be found.
- Users rely on copy-paste: Scammers know long alphanumeric wallet addresses are a nightmare to type by hand, and thus users will default to copy-pasting them. This is key for clipboard hijacking malware to work.
- No identity verification: Most crypto wallets don’t verify recipients, so any valid address is automatically accepted.
It must also be underlined that not all clipboard hijacking malware works the same way. CryptoShuffler, for instance, is one strain of malware that stole over $150,000 in Bitcoin that ran as a hidden background process in computers, while Qulab was a malware designed to run on Android smartphones that secretly installed itself when users downloaded fake “Tor Browser” apps from unofficial app stores like APKPure.
How to Detect Clipboard Hijacking Malware on Your Device
If you think your device might be infected, here are some ways to test it:
- Check your copy-pasted data. Go on Google, look up a random Bitcoin or Ethereum address, and copy it. Then paste it onto a notepad file or text editor, and compare the two alphanumeric wallet addresses. If they do not match, that is a clear sign a clipboard virus is installed on your device.
- Repeat the test multiple times, with different random addresses. Some clipboard hijacking malwares may only activate with specific cryptocurrencies, or every X number of copies to obfuscate its presence.
- Check for random slowdowns, crashes, or weird network activity on your device. Clipboard malware isn’t always perfectly optimised, and odd device performance might suggest there are secret processes running in the background.
Antivirus software like Malwarebytes and Kaspersky is also recommended to scan for clipboard malware, as some clipboard hijackers are highly sophisticated and expertly hidden.
How to Remove Clipboard Hijacker Malware
If you have confirmed an infection, or even suspect it, it’s best to act fast.
Manual Steps:
- Check startup apps: On Windows, hit Win + R, type msconfig, and look under the Startup tab for suspicious entries. If you find any, disable them.
- Inspect Task Manager: Look for rogue processes (e.g., “AutoIt v3 Script”) and end them. If you see any names that look legitimate, but you do not recognise them, google them.
- Uninstall shady software: Go to Control Panel > Programs and remove anything you don’t trust, especially recent downloads.
- Check your browser extensions: Some clipboard hijackers disguise themselves as extensions. Go into your browser and make sure you disable any extensions you do not recognise.
Clipboard Hijacker Removal Tools:
After carrying out a manual checkup of your device, it is highly recommended you run a scan with a trusted antivirus software. Here are our recommendations:
- Malwarebytes and Kaspersky are great antivirus softwares that will detect most trojans and hidden processes. Run a full scan, and get rid of the malware.
- HitmanPro por PC users and ComboCleaner for MacOS are more sophisticated software, designed around deep malware removal. Very useful if dealing with highly advanced clipboard hijackers.
Check for Persistence!
Malware doesn’t just go away; many of these programs leave hidden backups in your devices in case the main files are deleted. Restart your device and check again for any resurgence of the clipboard virus: run Task Manager, re-check your startup processes, and do another full scan with your antivirus of choice. Clipboard hijacker malware removal takes time and attention to detail. Don’t skip any steps!
Can You Recover Crypto Stolen by Clipboard Hijackers?
Short answer: no. If your crypto was stolen by a clipboard hijacker, it’s usually gone for good. Blockchain transactions are final, and there is no regulatory authority to appeal to. It is thankfully possible to track those funds, and at CNC Intelligence we’ve worked alongside law enforcement to investigate cases where clipboard hijackers were involved.
That said, the best course of action against clipboard hijacker malware is to shield yourself against it, and prevent your devices from being infected in the first place. Run regular scans with your antivirus, avoid downloading software from shady websites, and don’t open strange emails. For an extra layer of protection, keep an eye on your Task Manager, and every so often copy-paste a random crypto wallet address into Notepad. It might save you a headache.
How to Protect Yourself from Clipboard Hijacking in the Future:
Given the irreversible nature of blockchain transactions, protecting yourself against clipboard hijacker software is key. Here is how you can do it:
- Verify every address: Whenever you copy a wallet address, paste it somewhere safe, like Notepad, and triple-check it. Make sure it matches before hitting send.
- Use smart wallets: Apps like Trust Wallet, or hardware wallets like Ledger and Trezor, often confirm addresses on-screen.
- Secure your clipboard: After copying sensitive data, overwrite it with random text (ie “abc123”) or clear it via Settings > System > Clipboard (Windows).
- Use multi-factor authentication: Enable MFA on exchanges and wallets to block unauthorized access.
- Get a password manager: Tools like LastPass or 1Password are great alternatives to prevent having to copy-paste sensitive information.
- Avoid sketchy downloads: Stick to official app stores and verified sites.
These six steps may not be completely malware-proof, but following these guidelines will make your device exponentially harder to infiltrate, and thus keep your crypto funds far more secure.
Conclusion
Clipboard hijacking is a simple yet highly effective way for cybercriminals to steal cryptocurrencies. It preys upon users’ trust in copy-pasting data, is capable of striking across multiple platforms, and exploits the irreversible nature of blockchain transactions for theft. But, at its core, this malware is not invincible.
Whether you’re a victim seeking to prevent this from happening again, or simply a crypto user seeking to better protect your funds, awareness and proactive measures are your best shield. If you double check all addresses, scan your devices regularly, and avoid sketchy websites and downloads, the odds of your crypto being stolen go down dramatically.
Crypto malware evolves fast, so keep learning! Stay cautious, check your clipboard, and don’t let these pickpockets catch you off guard.
Bibliography:
The Record (2021). “Malware author made $560,000 just from a simple clipboard hijacker”.
Kaspersky (2025). “Kaspersky exposes hidden malware on GitHub stealing personal data and $485,000 in Bitcoin”.
Malwarebytes (2025). “Fake CAPTCHA websites hijack your clipboard to install information stealers”.
Bufferzone Security (2023). “Clipboard Hijacking attacks and How to Prevent Them”.
We offer complimentary consultations to determine if our Asset Tracing, Recovery Assistance, and Intelligence Services suit your case.
Your name, comment, and timestamp will be public when you comment. We also store this data, which may be used for research or content creation per our Privacy Policy. By commenting, you consent to these terms.